19. Mathematics
This module introduces how non-@ud mathematics are instrumented in Hoon. It may be considered optional and skipped if you are speedrunning Hoon School.
All of the math we've done until this point relied on unsigned integers: there was no negative value possible, and there were no numbers with a fractional part. How can we work with mathematics that require more than just bare unsigned integers?
@u unsigned integers (whether @ud decimal, @ux hexadecimal, etc.) simply count upwards by binary place value from zero. However, if we apply a different interpretive rule to the resulting value, we can treat the integer (in memory) as if it corresponded to a different real value, such as a negative number or a number with a fractional part. Auras make this straightforward to explore:
> `@ud`1.000.000
1.000.000
> `@ux`1.000.000
0xf.4240
> `@ub`1.000.000
0b1111.0100.0010.0100.0000
> `@sd`1.000.000
--500.000
> `@rs`1.000.000
.1.401298e-39
> `@rh`1.000.000
.~~3.125
> `@t`1.000.000
'@B\0f'How can we actually treat other modes of interpreting numbers as mathematical quantities correctly? That's the subject of this lesson.
(Ultimately, we are using a concept called Gödel numbering to justify mapping some data to a particular representation as a unique integer.)
Floating-Point Mathematics
A number with a fractional part is called a “floating-point number” in computer science. This derives from its solution to the problem of representing the part less than one.
Consider for a moment how you would represent a regular decimal fraction if you only had integers available. You would probably adopt one of three strategies:
Rational numbers. Track whole-number ratios like fractions. Thus 1.25=45, thence the pair
(5, 4). Two numbers have to be tracked: the numerator and the denominator.Fixed-point. Track the value in smaller fixed units (such as thousandths). By defining the base unit to be 10001 , 1.25 may be written 1250. One number needs to be tracked: the value in terms of the scale. (This is equivalent to rational numbers with only a fixed denominator allowed.)
Floating-point. Track the value at adjustable scale. In this case, one needs to represent 1.25 as something like 125×10−2. Two numbers have to be tracked: the significand (125) and the exponent (−2).
Most systems use floating-point mathematics to solve this problem. For instance, single-precision floating-point mathematics designate one bit for the sign, eight bits for the exponent (which has 127 subtracted from it), and twenty-three bits for the significand.
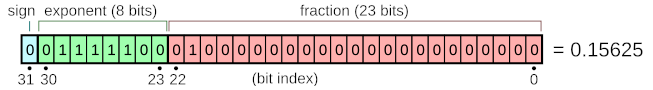
This number, 0b11.1110.0010.0000.0000.0000.0000.0000, is converted to decimal as (−1)0×2(124−127)×1.25=2−3×1.25=0.15625.
(If you want to explore the bitwise representation of values, this tool allows you to tweak values directly and see the results.)
Hoon Operations
Hoon utilizes the IEEE 754 implementation of floating-point math for four bitwidth representations.
@r
Floating-point value
@rh
Half-precision 16-bit mathematics
.~~4.5
@rs
Single-precision 32-bit mathematics
.4.5
@rd
Double-precision 64-bit mathematics
.~4.5
@rq
Quadruple-precision 128-bit mathematics
.~~~4.5
There are also a few molds which can represent the separate values of the FP representation. These are used internally but mostly don't appear in userspace code.
As the arms for the four @r auras are identical within their appropriate core, we will use @rs single-precision floating-point mathematics to demonstrate all operations.
Conversion to and from other auras
Any @ud unsigned decimal integer can be directly cast as a @rs.
However, as you can see here, the conversion is not “correct” for the perceived values. Examining the @ux hexadecimal and @ub binary representation shows why:
If you refer back to the 32-bit floating-point example above, you'll see why: to represent one exactly, we have to use 1.0=(−1)0×2127−127×1 and thus 0b11.1111.1000.0000.0000.0000.0000.0000.
So to carry out this conversion from @ud to @rs correctly, we should use the +sun:rs arm.
To go the other way requires us to use an algorithm for converting an arbitrary number with a fractional part back into @ud unsigned integers. The +fl named tuple representation serves this purpose, and uses the Dragon4 algorithm to accomplish the conversion:
It's up to you to decide how to handle this result, however! Perhaps a better option for many cases is to round the answer to a @s integer with +toi:rs:
(@s signed integer math is discussed below.)
Floating-point specific operations
As with aura conversion, the standard mathematical operators don't work for @rs:
The +rs core defines a set of @rs-affiliated operations which should be used instead:
This includes:
+add:rs, addition.+sub:rs, subtraction.+mul:rs, multiplication.+div:rs, division.+gth:rs, greater than.+gte:rs, greater than or equal to.+lth:rs, less than.+lte:rs, less than or equal to.+equ:rs, check equality (but not nearness!).+sqt:rs, square root.
Exercise: +is-close
+is-closeThe +equ:rs arm checks for complete equality of two values. The downside of this arm is that it doesn't find very close values:
Produce an arm which check for two values to be close to each other by an absolute amount. It should accept three values: a, b, and atol. It should return the result of the following comparison:
Tutorial: Length Converter
Write a generator to take a @tas input measurement unit of length, a @rs value, and a @tas output unit to which we will convert the input measurement. For instance, this generator could convert a number of imperial feet to metric decameters.
/gen/convert-length.hoon
This program shows several interesting aspects, which we've covered before but highlight here:
Meters form the standard unit of length.
~|sigbar produces an error message in case of a bad input.+$lusbuc is a type constructor arm, here for a type union over units of length.
Exercise: Measurement Converter
Add to this generator the ability to convert some other measurement (volume, mass, force, or another of your choosing).
Add an argument to the cell required by the gate that indicates whether the measurements are distance or your new measurement.
Enforce strictly that the
fr-measandto-measvalues are either lengths or your new type.Create a new map of conversion values to handle your new measurement conversion method.
Convert the functionality into a library.
+rs as a Door
+rs as a DoorWhat is +rs? It's a door with 21 arms:
The battery of this core, pretty-printed as 21|ezj, has 21 arms that define functions specifically for @rs atoms. One of these arms is named +add; it's a different +add from the standard one we've been using for vanilla atoms, and thus the one we used above. When you invoke +add:rs instead of just +add in a function call, (1) the .rs door is produced, and then (2) the name search for +add resolves to the special +add arm in .rs. This produces the gate for adding @rs atoms:
What about the sample of the .rs door? The pretty-printer shows r=?(%d %n %u %z). The +rs sample can take one of four values: %d, %n, %u, and %z. These argument values represent four options for how to round @rs numbers:
%drounds down.%nrounds to the nearest value.%urounds up.%zrounds to zero.
The default value is %z, round to zero. When we invoke +add:rs to call the addition function, there is no way to modify the +rs door sample, so the default rounding option is used. How do we change it? We use the ~( ) notation: ~(arm door arg).
Let's evaluate the +add arm of +rs, also modifying the door sample to %u for 'round up':
This is the gate produced by +add, and you can see that its sample is a pair of @rs atoms. But if you look in the context you'll see the rs door. Let's look in the sample of that core to make sure that it changed to %u. We'll use the wing +6.+7 to look at the sample of the gate's context:
It did indeed change. We also see that the door sample uses the face .r, so let's use that instead of the unwieldy +6.+7:
We can do the same thing for rounding down, %d:
Let's see the rounding differences in action. Because ~(add rs %u) produces a gate, we can call it like we would any other gate:
This difference between rounding up and rounding down might seem strange at first. There is a difference of 0.0000003 between the two answers. Why does this gap exist? Single-precision floats are 32-bit and there's only so many distinctions that can be made in floats before you run out of bits.
Just as there is a door for @rs functions, there is a Hoon standard library door for @rd functions (double-precision 64-bit floats), another for @rq functions (quad-precision 128-bit floats), and one more for @rh functions (half-precision 16-bit floats).
Signed Integer Mathematics
Similar to floating-point representations, signed integer representations use an internal bitwise convention to indicate whether a number should be treated as having a negative sign in front of the magnitude or not. There are several ways to represent signed integers:
Sign-magnitude. Use the first bit in a fixed-bit-width representation to indicate whether the whole should be multiplied by −1, e.g.
0010.1011for 4310 and1010.1011for −4310. (This is similar to the floating-point solution.)One's complement. Use the bitwise
NOToperation to represent the value, e.g.0010.1011for 4310 and1101.0100for −4310. This has the advantage that arithmetic operations are trivial, e.g. 4310−4110 =0010.1011+1101.0110=1.0000.0001, end-around carry the overflow to yield0000.0010= 2. (This is commonly used in hardware.)Offset binary. This represents a number normally in binary except that it counts from a point other than zero, like
-256.ZigZag. Positive signed integers correspond to even atoms of twice their absolute value, and negative signed integers correspond to odd atoms of twice their absolute value minus one.
There are tradeoffs in compactness of representation and efficiency of mathematical operations.
Hoon Operations
@u-aura atoms are unsigned values, but there is a complete set of signed auras in the @s series. ZigZag was chosen for Hoon's signed integer representation because it represents negative values with small absolute magnitude as short binary terms.
@s
signed integer
@sb
signed binary
--0b11.1000 (positive)
-0b11.1000 (negative)
@sd
signed decimal
--1.000.056 (positive)
-1.000.056 (negative)
@sx
signed hexadecimal
--0x5f5.e138 (positive)
-0x5f5.e138 (negative)
The +si core supports signed-integer operations correctly. However, unlike the @r operations, @s operations have different names (likely to avoid accidental mental overloading).
To produce a signed integer from an unsigned value, use +new:si with a sign flag, or simply use +sun:si
To recover an unsigned integer from a signed integer, use +old:si, which returns the magnitude and the sign.
+sum:si, addition.+dif:si, subtraction.+pro:si, multiplication.+fra:si, division.+rem:si, modulus (remainder after division), b modulo a as@s.+abs:si, absolute value.+cmp:si, test for greater value (as index,>→--1,<→-1,=→--0).
To convert a floating-point value from number (atom) to text, use+scow or+r-co:co with+rlys (and friends):
Beyond Arithmetic
The Hoon standard library at the current time omits many transcendental functions, such as the trigonometric functions. It is useful to implement pure-Hoon versions of these, although they are not as efficient as jetted mathematical code would be.
Produce a version of +factorial which can operate on @rs inputs correctly.
Produce an exponentiation function +pow-n which operates on integer @rs only.
Using both of the above, produce the +sine function, defined by
Implement +cosine.
Implement +tangent.
As a stretch exercise, look up definitions for exp (e^x) and natural logarithm, and implement these. You can implement a general-purpose exponentiation function using the formula
(We will use these in subsequent examples.)
Exercise: Calculate the Fibonacci Sequence
The Binet expression gives the nth Fibonacci number.
Implement this analytical formula for the Fibonacci series as a gate.
Date & Time Mathematics
Date and time calculations are challenging for a number of reasons: What is the correct granularity for an integer to represent? What value should represent the starting value? How should time zones and leap seconds be handled?
One particularly complicating factor is that there is no Year Zero; 1 B.C. is immediately followed by A.D. 1. (The date systems used in astronomy differ from standard time in this regard, for instance.)
In computing, absolute dates are calculated with respect to some base value; we refer to this as the "epoch". Unix/Linux systems count time forward from Thursday 1 January 1970 00:00:00 UT, for instance. Windows systems count in 10⁻⁷ s intervals from 00:00:00 1 January 1601. The Urbit epoch is ~292277024401-.1.1, or 1 January 292,277,024,401 B.C.; since values are unsigned integers, no date before that time can be represented.
Time values, often referred to as "timestamps", are commonly represented by the UTC value. Time representations are complicated by offset such as timezones, regular adjustments like daylight savings time, and irregular adjustments like leap seconds. (Read Dave Taubler's excellent overview of the challenges involved with calculating dates for further considerations, as well as Martin Thoma's “What Every Developer Should Know About Time” (PDF).)
Hoon Operations
A timestamp can be separated into the time portion, which is the relative offset within a given day, and the date portion, which represents the absolute day.
There are two molds to represent time in Hoon: the @d aura, with @da for a full timestamp and @dr for an offset; and the $date / $tarp structure:
@da
Absolute date
~2022.1.1
~2022.1.1..1.1.1..0000
@dr
Relative date (difference)
~h5.m30.s12
~d1000.h5.m30.s12..beef
.now returns the @da of the current timestamp (in UTC).
To go from a @da to a $tarp, use +yell:
To go from a @da to a $date, use +yore:
To go from a $date to a @da, use +year:
To go from a $tarp to a @da, use+yule:
The Urbit date system correctly compensates for the lack of Year Zero:
The +yo core contains constants useful for calculating time, but in general you should not hand-roll time or timezone calculations.
Tutorial: Julian Day
Astronomers use the Julian day to uniquely denote days. (This is not to be confused with the Julian calendar.) The following core demonstrates conversion to and from Julian days using signed integer (@sd) and date (@da) mathematics.
Unusual Bases
Phonetic Base
The @q aura is similar to @p except for two details: it doesn't obfuscate names (as planets do) and it can be used for any size of atom without adjust its width to fill the same size. Prefixes and suffixes are in the same order as @p, however. Thus:
@q auras can be used as sequential mnemonic markers for values.
The +po core contains tools for directly parsing @q atoms.
Base-32 and Base-64
The base-32 representation uses the characters "0123456789abcdefghijklmnopqrstuv" to represent values. The digits are separated into collections of five characters separated by . dot.
The base-64 representation uses the characters 0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ-~ to represent values. The digits are separated into collections of five characters separated by . dot.
Randomness
Entropy
You previously saw entropy introduced when we discussed stateful random number generation. Let's dig into what's actually going on with entropy.
It is not straightforward for a computer, a deterministic machine, to produce an unpredictable sequence. We can either use a source of true randomness (such as the third significant digit of chip temperature or another hardware source) or a source of artificial randomness (such as a sequence of numbers the user cannot predict).
For instance, consider the sequence 3 1 4 1 5 9 2 6 5 3 5 8 9 7 9 3. If you recognize the pattern as the constant π, you can predict the first few digits, but almost certainly not more than that. The sequence is deterministic (as it is derived from a well-characterized mathematical process) but unpredictable (as you cannot a priori guess what the next digit will be).
Computers often mix both deterministic processes (called “pseudorandom number generators”) with random inputs, such as the current timestamp, to produce high-quality random numbers for use in games, modeling, cryptography, and so forth. The Urbit entropy value .eny is derived from the underlying host OS's /dev/urandom device, which uses sources like keystroke typing latency to produce random bits.
Random Numbers
Given a source of entropy to seed a random number generator, one can then use the +og door to produce various kinds of random numbers. The basic operations of +og are described in the lesson on subject-oriented programming.
Exercise: Implement a random-number generator from scratch
Produce a random stream of bits using the linear congruential random number generator.
The linear congruential random number generator produces a stream of random bits with a repetition period of 231. Numericist John Cook explains how LCGs work:
The linear congruential generator used here starts with an arbitrary seed, then at each step produces a new number by multiplying the previous number by a constant and taking the remainder by 231−1.
/gen/lcg.hoon
Can you verify that 1s constitute about half of the values in this bit stream, as Cook illustrates in Python?
Exercise: Produce uniformly-distributed random numbers
Using entropy as the source, produce uniform random numbers: that is, numbers in the range [0, 1] with equal likelihood to machine precision.
We use the LCG defined above, then chop out 23-bit slices using +rip to produce each number, manually compositing the result into a valid floating-point number in the range [0, 1]. (We avoid producing special sequences like NaN.)
Convert the above to a %say generator that can optionally accept a seed; if no seed is provided, use .eny.
Produce a higher-quality Mersenne Twister uniform RNG, such as per this method.
Exercise: Produce normally-distributed random numbers
Produce a normally-distributed random number generator using the uniform RNG described above.
The normal distribution, or bell curve, describes the randomness of measurement. The mean, or average value, is at zero, while points fall farther and farther away with increasingly less likelihood.
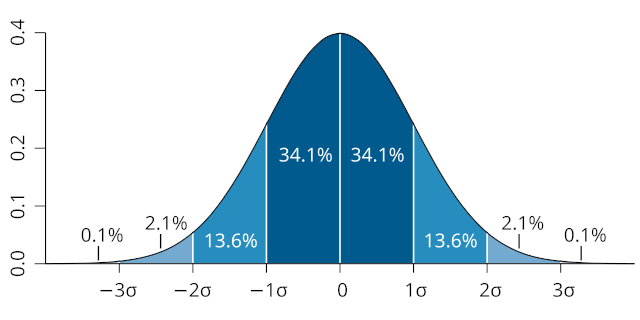
One way to get from a uniform random number to a normal random number is to use the uniform random number as the cumulative distribution function (CDF), an index into “how far” the value is along the normal curve.
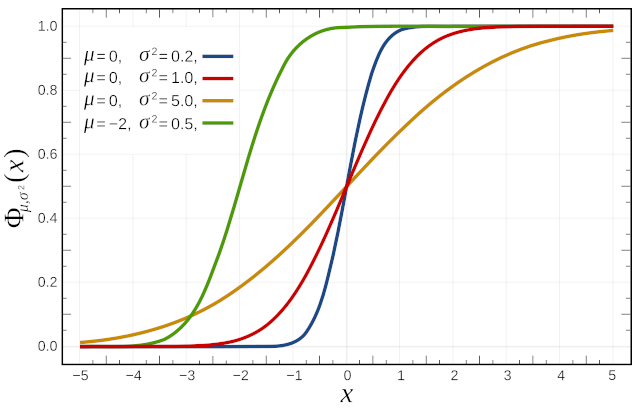
This is an approximation which is accurate to one decimal place:
where sgn is the signum or sign function.
To calculate an arbitrary power of a floating-point number, we require a few transcendental functions, in particular the natural logarithm and exponentiation of base e. The following helper core contains relatively inefficient but clear implementations of standard numerical methods.
Exercise: Upgrade the normal RNG
A more complicated formula uses several constants to improve the accuracy significantly:
where
sgn is the signum or sign function;
t is −ln[min(U,1−U)2]; and
the constants are:
c0=2.515517
c1=0.802853
c2=0.010328
d1=1.532788
d2=0.189268
d3=0.001308
Implement this formula in Hoon to produce normally-distributed random numbers.
How would you implement other random number generators?
Hashing
A hash function is a tool which can take any input data and produce a fixed-length value that corresponds to it. Hashes can be used for many purposes:
Encryption. A cryptographic hash function leans into the one-way nature of a hash calculation to produce a fast, practically-irreversible hash of a message. They are foundational to modern cryptography.
Attestation or preregistration. If you wish to demonstrate that you produced a particular message at a later time (including a hypothesis or prediction), or that you solved a particular problem, hashing the text of the solution and posting the hash publicly allows you to verifiably timestamp your work.
Data lookup. Hash tables are one way to implement a key→value mapping, such as the functionality offered by Hoon's
+map.
Theoretically, since the number of fixed-length hashes are finite, an infinite number of possible programs can yield any given hash. This is called a "hash collision", but for many practical purposes such a collision is extremely unlikely.
Hoon Operations
The Hoon standard library supports fast insecure hashing with +mug, which accepts any noun and produces an atom of the hash.
+mug operates on the raw form of the noun however, without Hoon-specific metadata like aura:
Hoon also includes SHA-256 and SHA-512 tooling. (+og, the random number generator, is based on SHA-256 hashing.)
+shax produces a hashed atom of 256 bits from any atom.
+shaz produces a hashed atom of 512 bits from any atom.
Exercise: Produce a secure password tool
Produce a basic secure password tool. It should accept a password, salt it (add a predetermined value to the password), and hash it. That hash is then compared to a reference hash to determine whether or not the password is correct.
Last updated